 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|
Certains malwares utilisent désormais le BSSID du point d’accès pour géolocaliser leurs victimes. Ils s’appuient pour cela sur des bases gratuites et accessibles à tous.
Le chercheur en sécurité Xavier Mertens a détecté une nouvelle méthode utilisée par les pirates pour géolocaliser leurs victimes et, le cas échéant, décider de leur sort. Habituellement, ils s’appuient sur l’adresse IP. Mais avec la pénurie d’adresses IPv4, il est de plus en plus difficile de géolocaliser cet identifiant avec certitude, car ces adresses sont de plus en plus échangées d’un opérateur à un autre et d’un pays à un autre.
Dans l’un des derniers codes malveillants analysés, Xavier Mertens a vu que l’auteur intégrait une seconde méthode : la géolocalisation par le BSSID (Basic Service Set Identifier). Cette séquence de 48 bits n’est rien d’autre que l’adresse MAC du point d’accès. Les 24 premiers bits désignent généralement le fournisseur. Les 24 bits restants sont choisis de telle manière à obtenir un identifiant unique de l’appareil. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?tag=Router

|
Scooped by
Gust MEES
|
You've heard about wardriving, but what about warshipping? Researchers at IBM X-Force Red have detailed a new tactic that they say can break into victims' Wi-Fi networks from far.
The company calls the technique warshipping, and it is a more efficient evolution of wardriving, a popular technique among hackers seeking access to any wireless network they can find. Whereas wardrivers drive around a wide area with a directional antenna looking for wireless networks to crack, IBM's researchers took a more targeted approach.
Speaking at Black Hat USA, IBM researchers explained how they used off-the-shelf components costing under $100 to create a single-board computer with Wi-Fi and 3G capability. This enables it to connect to a Wi-Fi network to harvest data locally and then send it to a remote location using its cellular connection. The small device runs on a cell phone battery and easily fits into a small package.
Attackers can then send the device to a company via regular mail, where it will probably languish in a mail room for a while. During this time, it can connect to any Wi-Fi networks it finds in the building and harvest data – typically a hashed network access code. It sends this back to the attacker, who can then use their own resources (or a cloud-based cracking service) to extract the original access code. At this point, they have access to the company's Wi-Fi network. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Internet+of+things https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Warshipping

|
Scooped by
Gust MEES
|
Earlier this year in April, two security researchers disclosed details about five vulnerabilities (collectively known as Dragonblood) in the WiFi Alliance's recently launched WPA3 WiFi security and authentication standard.
Yesterday, the same security researchers disclosed two new additional bugs impacting the same standard.
The two researchers -- Mathy Vanhoef and Eyal Ronen -- found these two new bugs in the security recommendations the WiFi Alliance created for equipment vendors in order to mitigate the initial Dragonblood attacks.
Just like the original Dragonblood vulnerabilities from April, these two new ones allow attackers to leak information from WPA3 cryptographic operations and brute-force a WiFi network's password. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=WiFi https://www.scoop.it/topic/securite-pc-et-internet/?&tag=WPA3 https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Dragonblood

|
Scooped by
Gust MEES
|
Public Wi-Fi is a great convenience that most of us – if not all of us – utilize regularly. There is little doubt, however, that using public Wi-Fi creates serious cybersecurity risks. At the same time, cybersecurity practitioners who preach that people should refrain from using public Wi-Fi are about as likely to succeed in their effort as someone telling people to abandon insecure computers and instead use un-hackable typewriters. As such, here are 9 suggestions as to how to use public Wi-Fi safely: Learn more / En savoir plus / Mehr erfahren: https://gustmees.wordpress.com/2013/05/27/dangers-of-wifi-in-public-places/

|
Scooped by
Gust MEES
|
A flaw in Hotspot Shield can expose VPN users, locations
The virtual private network says it provides a way to browse the web "anonymously and privately," but a security researcher has released code that could identify users' names and locations.
A security researcher has found a way to identify users of Hotspot Shield, a popular free virtual private network service that promises its users anonymity and privacy.
Hotspot Shield, developed by AnchorFree, has an estimated 500 million users around the world relying on its privacy service. By bouncing a user's internet and browsing traffic through its own encrypted pipes, the service makes it harder for others to identify individual users and eavesdrop on their browsing habits.
But an information disclosure bug in the privacy service results in a leak of user data, such as which country the user is located, and the user's Wi-Fi network name, if connected.
That information leak can be used to narrow down users and their location by correlating Wi-Fi network name with public and readily available data.
"By disclosing information such as Wi-Fi name, an attacker can easily narrow down or pinpoint where the victim is located," said Paulos Yibelo, who found the bug. Combined with knowing the user's country, "you can narrow down a list of places where your victim is located," he said.
ZDNet was able to independently verify Yibelo's findings by using his proof-of-concept code to reveal a user's Wi-Fi network. We tested on several machines and different networks, all with the same result.
VPNs are popular for activists or dissidents in parts of the world where internet access is restricted because of censorship, or heavily monitored by the state, as these services mask a user's IP addresses that can be used to pinpoint a person's real-world location.
Being able to identify a Hotspot Shield user in an authoritarian state could put them at risk!!! Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=VPN

|
Scooped by
Gust MEES
|
Der Sicherheitsstandard WPA2, der insbesondere zur Verschlüsselung von WLAN-Netzwerken empfohlen wird, ist über kritische Schwachstellen verwundbar. Betroffen sind demnach alle derzeit aktiven WLAN-fähigen Endgeräte in unterschiedlichen Ausprägungen. Das Bundesamt für Sicherheit in der Informationstechnik (BSI) rät dazu, WLAN-Netzwerke bis zur Verfügbarkeit von Sicherheits-Updates nicht für Online-Transaktionen wie Online Banking und Online Shopping oder zur Übertragung anderer sensitiver Daten zu nutzen.
"Nutzen Sie Ihr WLAN-Netzwerk so, als würden Sie sich in ein öffentliches WLAN-Netz einwählen, etwa in Ihrem Lieblings-Café oder am Bahnhof. Verzichten Sie auf das Versenden sensibler Daten oder nutzen Sie dazu einen VPN-Tunnel. Auch das kabelgebundene Surfen ist weiterhin sicher. Unternehmen sollten ihre Mitarbeiter sensibilisieren und geeignete Maßnahmen zur Absicherung ihrer Firmennetzwerke ergreifen. Sicherheitsupdates wurden bereits von verschiedenen Herstellern angekündigt und sollten umgehend durch den Nutzer eingespielt werden, sobald sie zur Verfügung stehen," erklärt Arne Schönbohm, Präsident des BSI. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/21st-century-learning-and-teaching/?&tag=VPN

|
Scooped by
Gust MEES
|
Le Wi-Fi n'a pas été conçu pour résister aux défis du XXIe siècle en matière de cyber sécurité. De nombreux experts recommandent donc la prudence lors de son utilisation. Une bonne nouvelle, toutefois. En réalité, les internautes ont déjà, depuis de nombreuses années, affaire aux dangers des connexions Wi-Fi non-sécurisées… Mais ils peuvent sécuriser leur réseau en prenant quelques précautions de base. Voici les meilleures façons de se protéger de KrackAttacks ou d’autres menaces ciblant les internautes via leurs connexions Wi-Fi : - Utilisez un VPN
Un VPN (réseau privé virtuel), tel que FREEDOME de F-Secure, chiffre vos données en transit. Il s’agit d’une excellente façon de sécuriser vos informations lorsque vous utilisez le Wi-Fi. Cet outil est même indispensable à votre sécurité lorsque vous utilisez un réseau Wi-Fi public. - Mettez vos appareils à jour
Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/21st-century-learning-and-teaching/?&tag=VPN

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
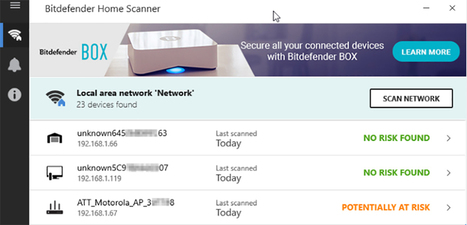
À l’heure où la sécurité des objets connectés fait toujours débat, l’éditeur de sécurité Bitdefender lance un outil gratuit permettant d’analyser l’intégralité des appareils connectés au réseau domestique. Un outil de prévention et de promotion pour les produits payants de l’éditeur, dont la récente Bitdefender Box. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=iot

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Gogo, the inflight Wi-Fi provider, is used by millions of airline passengers each year to stay connected while flying the friendly skies. But if you think the long arm of government surveillance doesn't have a vertical reach, think again.
According to a letter Gogo submitted to the Federal Communications Commission, the company voluntarily exceeded the requirements of the Communications Assistance for Law Enforcement Act, or CALEA, by adding capabilities to its service at the request of law enforcement. The revelation alarms civil liberties groups, which say companies should not be cutting deals with the government that may enhance the ability to monitor or track users.
“CALEA itself is a massive infringement on user’s rights,” says Peter Eckersley of the Electronic Frontier Foundation. “Having ISP’s [now] that say that CALEA isn’t enough, we’re going to be even more intrusive in what we collect on people is, honestly, scandalous.” Gogo provides inflight Wi-Fi and digital entertainment to Delta, American Airlines, Alaska Airlines, Virgin America, US Airways and others using a dedicated air-to-ground network that GoGo says it designed in consultation with law enforcement.
|

|
Scooped by
Gust MEES
|
Lors de la conférence sur la sécurité RSA 2020 qui avait lieu la semaine dernière à San Francisco, les chercheurs en sécurité de la société slovaque antivirus ESET ont présenté des détails sur une nouvelle vulnérabilité qui affecte les communications WiFi.
Nommé Kr00k, ce bug peut être exploité par un attaquant pour intercepter et décrypter un certain type de trafic réseau WiFi (s'appuyant sur les connexions WPA2).
Selon ESET, Kr00k affecte tous les appareils compatibles WiFi fonctionnant sur des puces Wi-Fi Broadcom et Cypress. Ce sont deux des chipsets WiFi les plus populaires au monde, et ils sont inclus dans de nombreux appareils, allant des ordinateurs portables aux smartphones, et des points d'accès aux haut-parleurs intelligents et autres objets connectés. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet/?&tag=WLAN https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Kr00k

|
Scooped by
Gust MEES
|
Dragonblood: Neue Lücken in WLAN-Verschlüsselung WPA3 könnten WPA3.1 nötig machen
Während Gerätehersteller fleißig das löchrige WPA3 in Produkte integrieren, sieht es so aus, als ob neue Lücken eine nicht-kompatible Version 3.1 nötig machen.
Das Schlüsselaustausch-Protokoll von WPA3 ist nach der Insekten-Ordnung der Libellen benannt (englisch: dragonfly). (Bild: Pixabay )
Im April hatten die beiden Sicherheitsforscher Mathy Vanhoef und Eyal Ronen ernste Sicherheitslücken in der Passwörtprüfung des neuen WLAN-Sicherheitsstandards WPA3 entdeckt und Dragonblood getauft. Vanhoef war mit der Entdeckung des KRACK-Angriffs auf WPA2 im Jahr 2017 überhaupt erst dafür verantwortlich gewesen, dass die Standardisierungsorganisation Wi-Fi Alliance den WPA3-Standard entwickelt hatte.
Nun sieht es so aus, als könnten durch Vanhoef und Ronen neu veröffentlichte Dragonblood-Lücken dafür sorgen, dass ein WPA3.1 aus der Taufe gehoben werden muss. Diese neue Version des Sicherheits-Standards wäre nicht abwärtskompatibel zu WPA3. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=WiFi https://www.scoop.it/topic/securite-pc-et-internet/?&tag=WPA3 https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Dragonblood

|
Scooped by
Gust MEES
|
A new way to compromise the WPA/WPA2 security protocols has been accidentally discovered by a researcher investigating the new WPA3 standard.
The attack technique can be used to compromise WPA/WPA2-secured routers and crack Wi-Fi passwords which have Pairwise Master Key Identifiers (PMKID) features enabled.
Security researcher and developer of the Hashcat password cracking tool Jens "Atom" Steube made the discovery and shared the findings on the Hashcat forum earlier this month.
At the time, Steube was investigating ways to attack the new WPA3 security standard. Announced in January by industry body the Wi-Fi Alliance, WPA3 is the latest refresh of the Wi-Fi standard.
WPA3 aims to enhance user protection, especially when it comes to open Wi-Fi networks and hotspots commonly found in public spaces, bars, and coffee shops. The new standard will utilize individualized data encryption to scramble connections -- as well as new protections against brute-force attempts to crack passwords.
However, the aging WPA2 standard has no such protection. Learn more / En savoir plus / Mehr erfahren: https://gustmees.wordpress.com/2013/05/27/dangers-of-wifi-in-public-places/ https://www.scoop.it/t/securite-pc-et-internet/?&tag=WiFi

|
Scooped by
Gust MEES
|
Wi-Fi devices have been using the same security protocol for over a decade. But today, that’ll begin to change: the Wi-Fi Alliance, which oversees adoption of the Wi-Fi standard, is beginning to certify products that support WPA3, the successor to the WPA2 security protocol that’s been in use since 2004.
The new protocol provides a number of additional protections for devices connected over Wi-Fi. One big improvement makes it harder for hackers to crack your password by guessing it over and over again, and another limits what data hackers can see even once they’ve uncovered the passcode. Nothing will change as far as users see it; you’ll still just type in your password and connect to the network.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=WiFi https://www.scoop.it/t/securite-pc-et-internet/?&tag=WPA2

|
Scooped by
Gust MEES
|
The company last week quietly patched vulnerabilities in the WPA2 protocol used to secure wireless networks, but did not reveal the fix until today. Microsoft today revealed that it quietly patched Windows last week against vulnerabilities in the Wi-Fi Protected Access II (WPA2) protocol used to secure wireless networks. Details of the security update were only published Monday to Microsoft's Security Update Guide, the catalog-like portal that earlier this year replaced the decades-old practice of delivering explanatory bulletins. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=WPA2 http://www.scoop.it/t/21st-century-learning-and-teaching/?&tag=VPN

|
Scooped by
Gust MEES
|
Here's what you need to know about KrackAttacks, and what you can do to protect yourself. And there’s the silver lining. We’ve actually been living with the risks created by insecure Wi-Fi connections for many years, and users can protect themselves by taking some basic security precautions. Here’s the best ways to stay safe from KrackAttacks and other threats targeting people through their Wi-Fi connections: Use a VPN A VPN (virtual private network), such as F-Secure Freedome encrypts your data while it’s in transit. This is a great way to secure your information when using Wi-Fi, and should be considered essential when using a publicly accessible Wi-Fi network. Update your devices Attacking routers is a means to an end for attackers. What they’re really after are your devices. They want to steal your credit card info, passwords, and other data. And that’s what the KrackAttacks are actually doing. Updating your devices’ software and operating systems is sound security advice, so use this as a reminder to make sure your desktops, laptops, phone, and tablets are all updated. Update your routers Routers have a long history of security problems. They’re often poorly supported by device vendors (and in some cases not at all). You should check your router’s settings to see if there’s a firmware update available, or possibly the website of your router’s manufacturer or vendor. If you’re not getting security updates for your router, consider getting one built to be secure. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/21st-century-learning-and-teaching/?&tag=VPN

|
Scooped by
Gust MEES
|
Le WPA2 est un protocole de sécurité très utilisé pour le Wi-Fi et, mauvaise nouvelle, il est vulnérable. En effet, des experts en sécurité informatique ont mis à jour plusieurs failles permettant d'écouter, d'intercepter et d'agir sur les appareils connectés. Des chercheurs en informatique viennent de révéler l'existence d'un nouvel "exploit" baptisé KRACK (pour Key Reinstallation Attacks), mettant directement en cause la sécurité des réseaux Wi-Fi. En effet, il permet a priori de tirer parti des vulnérabilités du Wi-Fi pour autoriser des hackers à opérer une surveillance sur les données transitant entre un point d'accès sans fil et les ordinateurs qui y sont connectés.
Comme le relèvent nos confrères d'Ars Technica, les experts en sécurité à l'origine de cette découverte ont exploité plusieurs failles se situant au niveau de la gestion des clés du protocole de sécurité WPA2 pour valider l'existence de cette brèche et en apporter la preuve. Précisons qu'en 13 ans d'existence, c'est la première fois que la sécurité du protocole WPA2 est mise à mal.
Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/21st-century-learning-and-teaching/?&tag=VPN

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
An advanced hacking and cyberespionage campaign against high-value targets has returned.
The so-called 'DarkHotel' group has been active for over a decade, with a signature brand of cybercrime that targets business travellers with malware attacks, using the Wi-Fi in luxury hotels across the globe.
Hotel Wi-Fi hotspots are compromised in order to help deliver the payload to the selected pool of victims. The exact methods of compromise remain uncertain, but cybersecurity experts believe it involves attackers remotely exploiting vulnerabilities in server software or infiltrating the hotel and gaining physical access to the machines. Learn more / En savoir plus / Mehr erfahren: https://gustmees.wordpress.com/2013/05/27/dangers-of-wifi-in-public-places/ http://www.scoop.it/t/securite-pc-et-internet/?&tag=WiFi

|
Scooped by
Gust MEES
|
Le hacking, désormais, est d’une simplicité enfantine.... Même les non-hackers s'y amusent ! Prenons le Wi-Fi public, par exemple. Pour espionner la navigation web de clients qui sirotent tranquillement leur café dans une brasserie avec Wi-Fi gratuit, pas besoin d’être un pro. Learn more / En savoir plus / Mehr erfahren: https://gustmees.wordpress.com/2013/05/27/dangers-of-wifi-in-public-places/

|
Scooped by
Gust MEES
|
Late last month, a Siamese cat named Coco went wandering in his suburban Washington, DC neighborhood. He spent three hours exploring nearby backyards. He killed a mouse, whose carcass he thoughtfully brought home to his octogenarian owner, Nancy. And while he was out, Coco mapped dozens of his neighbors’ Wi-Fi networks, identifying four routers that used an old, easily-broken form of encryption and another four that were left entirely unprotected.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Cats+as+wardriver

|
Scooped by
Gust MEES
|
|



 Your new post is loading...
Your new post is loading...





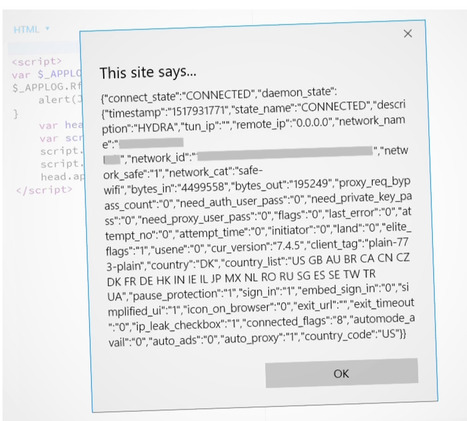

















Certains malwares utilisent désormais le BSSID du point d’accès pour géolocaliser leurs victimes. Ils s’appuient pour cela sur des bases gratuites et accessibles à tous.
Le chercheur en sécurité Xavier Mertens a détecté une nouvelle méthode utilisée par les pirates pour géolocaliser leurs victimes et, le cas échéant, décider de leur sort. Habituellement, ils s’appuient sur l’adresse IP. Mais avec la pénurie d’adresses IPv4, il est de plus en plus difficile de géolocaliser cet identifiant avec certitude, car ces adresses sont de plus en plus échangées d’un opérateur à un autre et d’un pays à un autre.
Dans l’un des derniers codes malveillants analysés, Xavier Mertens a vu que l’auteur intégrait une seconde méthode : la géolocalisation par le BSSID (Basic Service Set Identifier). Cette séquence de 48 bits n’est rien d’autre que l’adresse MAC du point d’accès. Les 24 premiers bits désignent généralement le fournisseur. Les 24 bits restants sont choisis de telle manière à obtenir un identifiant unique de l’appareil.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/securite-pc-et-internet/?tag=Router